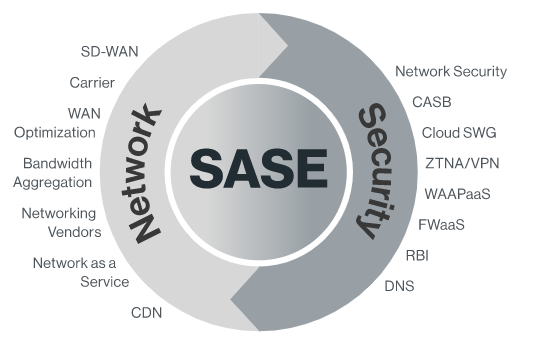
SASE – Core Value
- Infrastructure Convergence (All-In-One Platform)
- Flexibility & Reduced Network Complexity (Business Agility)
- Manageable Detection and Response (Security Unified Platform)
- Private Backbone for Corporate (Performance)

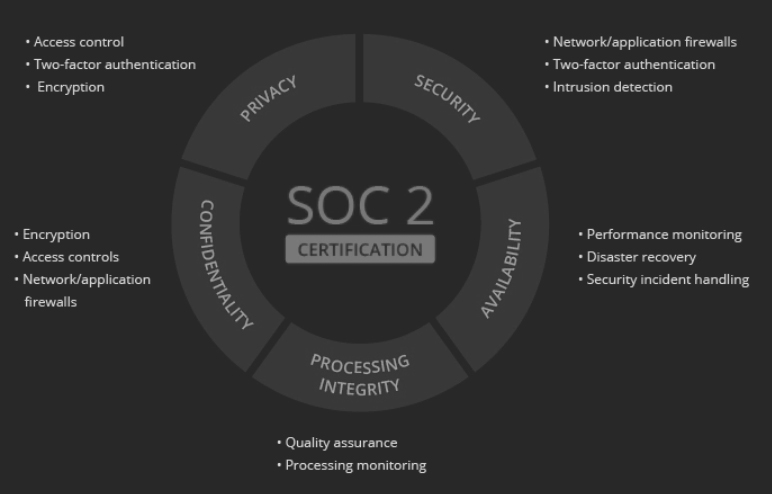
CATO has several certification and standards to Information Security.
Cato SASE cloud is a global converged cloud-native service that securely and optimally connects all branches, datacenters, people, and clouds. Cato can be gradually deployed to replace or augment legacy network services and security point solutions.
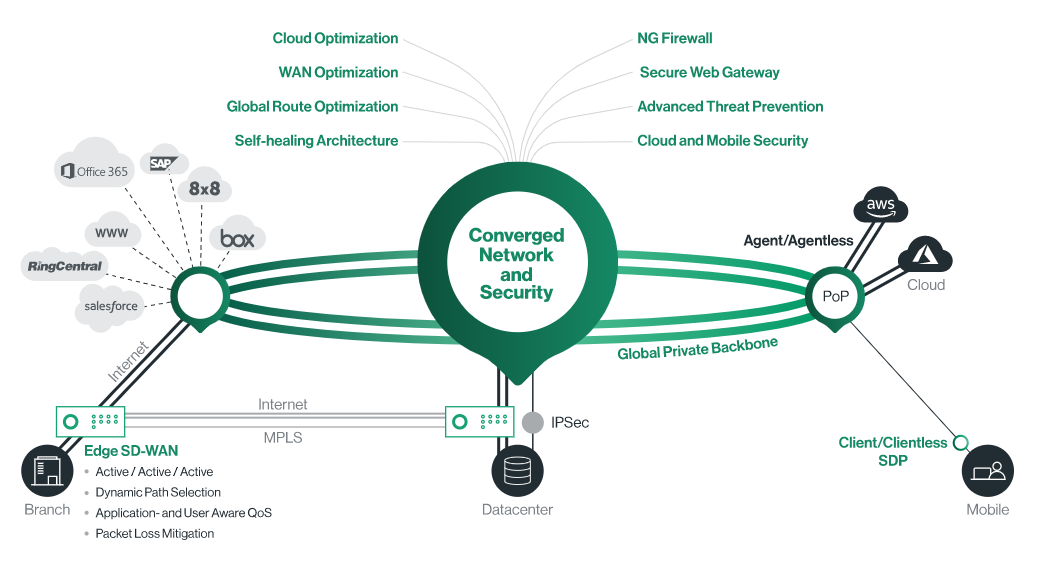
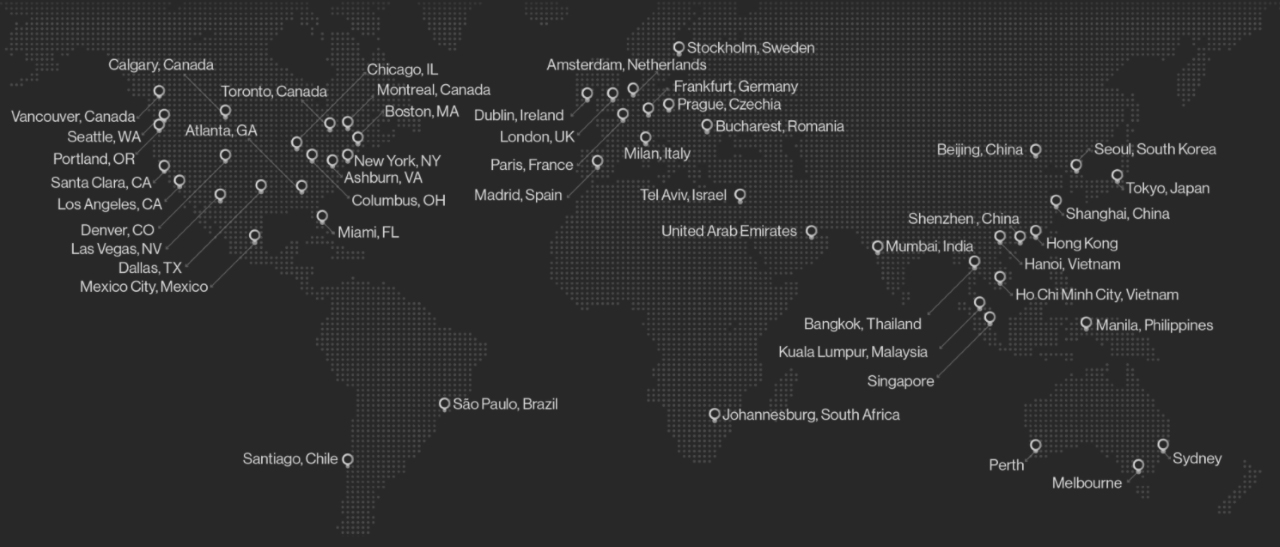
Cato SASE Cloud runs on a private global backbone of 65+ PoPs connected via multiple SLA-backed network providers. The PoPs software continuously monitors the providers for latency, packet loss, and jitter to determine, in real-time, the best route for every packet.
Cato’s backbone design delivers end-to-end route optimization for WAN and cloud traffic, and a self-healing architecture for maximum service uptime. Our customers experience connectivity that is superior to the unpredictable public Internet and more affordable than global MPLS and other legacy backbones.
Cato integrates with major cloud providers, such as Amazon AWS, Microsoft Azure, and Google Cloud with secure IPSec tunnels. By using its global backbone to optimally route traffic from the edge to the cloud providers, Cato eliminates the need for premium cloud connectivity solutions such as AWS DirectConnect and Microsoft Azure ExpressRoute.
The integration is agentless and connecting a cloud datacenter to Cato takes minutes. There is no need to deploy or pay for cloud server instances. Lastly, all traffic is subject to full security inspection with Cato’s built-in security stack.
Cato SASE Cloud provides users with zero trust network access (SDP/ZTNA) to on-premises and cloud applications using laptops, tablets, and smartphones. With a Cato Client or Clienteles browser access, users securely connect to the nearest Cato PoP using strong Multi-Factor Authentication. Traffic flows only to applications authorized for the users based on identity, access policy, and user context. Throughout the session, traffic is fully inspected by Cato’s security stack to prevent malware propagation from compromised endpoints.